Case Study:
SBB
The Challenge
The connectivity problem
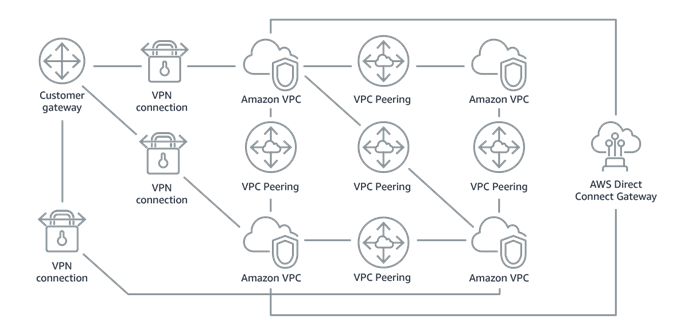
In the journey to the Cloud, many companies face the challenge of having to interconnect multiple on-premises workloads with their cloud workloads. While segmentation is key to network design in order to have a secure architecture, interconnecting several networks can be challenging, especially from the point of view of scalability and manageability. Typically, connecting on-premises offices and data centers to the cloud requires the use of point-to-point connections, such as IPsec Virtual Private network (VPN) tunnels or private network fiber connections. Connecting virtual networks (groups of networked cloud resources) with each other also requires point-to-point connections. However, as the number of on-premises offices and virtual networks increases, the number of point-to-point connections grows, resulting in a large mesh network that can be difficult, cumbersome, and costly to manage. Organizations using AWS have typically used AWS Direct Connect and AWS Site-to-Site Virtual Private Network (VPN) connections for connecting their on-premises environment to individual Amazon VPCs and VPC peering for connecting their Amazon VPCs with each other.
The main problem of such a scenario is that setting up VPC peering connections between separate accounts became unmanageable and cumbersome. For a VPC peering connection to be established, one account sends the connection request, while the other account must accept it.
The account accepting the request must manually configure the Amazon VPC to accommodate the new connection. While this may be a simple process when dealing with a small number of connections, SBB anticipated repeating this process and reconfiguring connections as part of their normal operations
This root problem, generates many other issues:
- Networking becomes fast too complex to manage
- Automation is challenging, as VPC peering requires manual intervention.
- Level of visibility and control over traffic flow is reduced.
- Monitoring of traffic becomes challenging, as multiple logs need to be collected from different sources and accounts.
The following diagram summarizes the peering architecture.
The Solution
AWS Transit Gateway
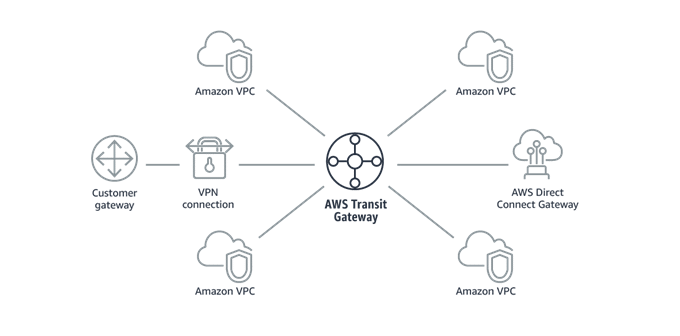
AWS Transit Gateway simplifies how organizations connect their Amazon VPCs with one another and to their on-premises networks within a region by serving as a central point for Layer 3 network connectivity. By enabling a “hub-and-spoke” topology, the solution can help organizations reduce the number of VPC peering connections and consolidate access to the on-premises network.
Even though the number of VPCs is small and there is only one enterprise location in the previous figure, it is easy to see how the Transit Gateway simplifies the environment. Imagine how much complexity is removed when there are additional enterprise locations and hundreds or thousands of Amazon VPCs. Now, organizations can simply connect their on-premises networks and Amazon VPCs via AWS Transit Gateway.
Integrating cloud and on-premises IT environments remains a challenge for organizations when pursuing a hybrid cloud strategy. A necessary part of that integration is ensuring that resources both in the cloud and on-premises locations are networked to respond to business needs without the need for extensive architecture planning, management, and administration.
AWS Transit Gateway enables organizations to network their cloud and on-premises environments. With this managed, distributed, and scalable service, large enterprises can develop global private networks connecting on-premises locations to Amazon VPCs in any AWS region without the need for multiple point-to-point connections. Enterprises can leverage AWS Transit Gateway Network Manager to monitor the performance and availability of their AWS Transit Gateways and corresponding attachments. AWS Transit Gateway also offers other features that help organizations to build out and manage global enterprise-grade networks. With AWS Transit Gateway, organizations can ultimately decrease the time and resources required to deploy and manage a global network architecture with less complexity, decreasing both network infrastructure and operational costs.
Tools & Technologies
Implementation on AWS
As in this case the main target it’s to separate the traffic from the VPC’s and ensure that external companies connecting through VPN can only access the respective workloads on their VPC, the architecture we decided to implement consists on using 2 different routing tables, one for the VPN, allowing only the routes to the relevant VPC’s and restricting the access to the on-premises network, and another for the VPC’s, which ensures the no interconnection between accounts and VPC’s and allows only northbound-southbound traffic (VPC-VPN and back).
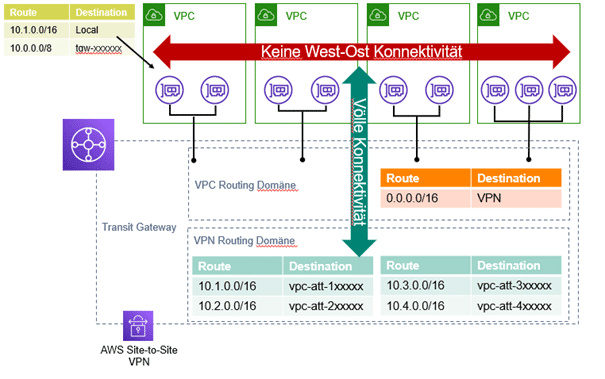
Results & Benefits
Benefit 1
One of the key properties of this implementation is the simplification of the network connectivity: Instead of multiple VPN connections for each of the accounts/VPC’s we use only one VPN connected to the Transit Gateway and manage all the traffic through the Transit Gateway.
Benefit 2
Isolation is key to ensure security, especially when connecting the company’s network infrastructure with external/3rd party datacenters. By using AWS Transit Gateway it’s easy to control the network routing in a centralized routing table, having therefore a better overlook and making the security policies easier to enforce and manage.
Benefit 3
As Transit Gateway it’s an AWS Managed Service, it integrates seamlessly with other AWS Tools, like CloudTrail, CloudWatch, IAM, making it easier for operation and security teams to monitor and automate the deployments. Using IAM, you can create and manage AWS users and groups, and use permissions to allow and deny their access to the AWS Transit Gateway. AWS Transit Gateway provides statistics and logs that are then used by services such as Amazon CloudWatch and Amazon VPC Flow Logs. You can use Amazon CloudWatch to get bandwidth usage between Amazon VPCs and a VPN connection, packet flow count, and packet drop count. You can also enable Amazon VPC Flow Logs on AWS Transit Gateway so you can capture information on the IP traffic routed through the AWS Transit Gateway. AWS Transit Gateway Network Manager includes events and metrics to monitor the quality of your global network, both in AWS and on premises. Event alerts specify changes in the topology, routing, and connection status. Usage metrics provide information on up/down connection, bytes in/out, packets in/out, and packets dropped.
Conclusion
Transit Gateway is the key for multi-account multi-VPC connectivity scenarios, simplifying the connectivity in complex networks, offering a superior manageability, scalability and security than other solutions. In the modern IT environments, where automation is key, once you’ve registered existing AWS Transit Gateways, the Network Manager automatically identifies the Site-to-Site VPN connections and the on-premises resources with which they are associated. The SD-WAN consoles from vendors that have integrated AWS Transit Gateway, such as Cisco, Aruba, Silver Peak, or Aviatrix, automatically provision new AWS Site-to-Site VPN connections in Transit Gateway Network Manager and automate the definition of your on-premises network in Transit Gateway Network Manager. You can also manually define your on-premises network in Transit Gateway Network Manager


Kunde
SBB
SBB is the federal railway company in Switzerland. With more than 300 million journeys per year and more than 3.000km of track infrastructure, it is known worldwide for the quality of its services and its punctuality. Today, SBB is already purchasing public cloud services from AWS for innovation projects. SBB wants to progressively move more workloads to the public cloud.
Partner
AWS
As AWS Advanced Consulting and training partner, we support Swiss customers on their way to the cloud. Cloud-native technologies are part of our DNA. Since the company’s foundation (2011), we have been accompanying cloud projects, implementing and developing cloud-based solutions.